Hi Everyone,
I’m happy to share that this issue features a special guest: Leonida Reitano, the organizer of the upcoming OsintifyCON (February 5th).
In this edition, Leonida shares the personal inspiration behind bringing this event to life. It is a rare glimpse behind the curtain because often, the people creating these events stand in the shadow of the show itself. Today, we are bringing the organizer into the spotlight.
Leonida is a veteran of the trade a highly respected practitioner and educator who has shaped how hundreds of analysts approach their work. His expertise goes far beyond tools; he specializes in applied methodologies, operational efficiency, and, crucially, investigator safety.
He has trained hundreds of professionals, including police officers, corporate investigators, intelligence analysts, fraud analysts, journalists, and private investigators. Organizations whose personnel he has trained include Kroll, UniCredit, AgustaWestland, Admiral Group, ACFE, RCS Mediagroup, and the Counterterrorism Division of the Italian National Police. As a certified Social Links instructor and author of the best-selling handbook Esplorare Internet, Leonida brings deep tactical knowledge to the table.
But first, let’s dive into the latest news.
Cybersecurity News
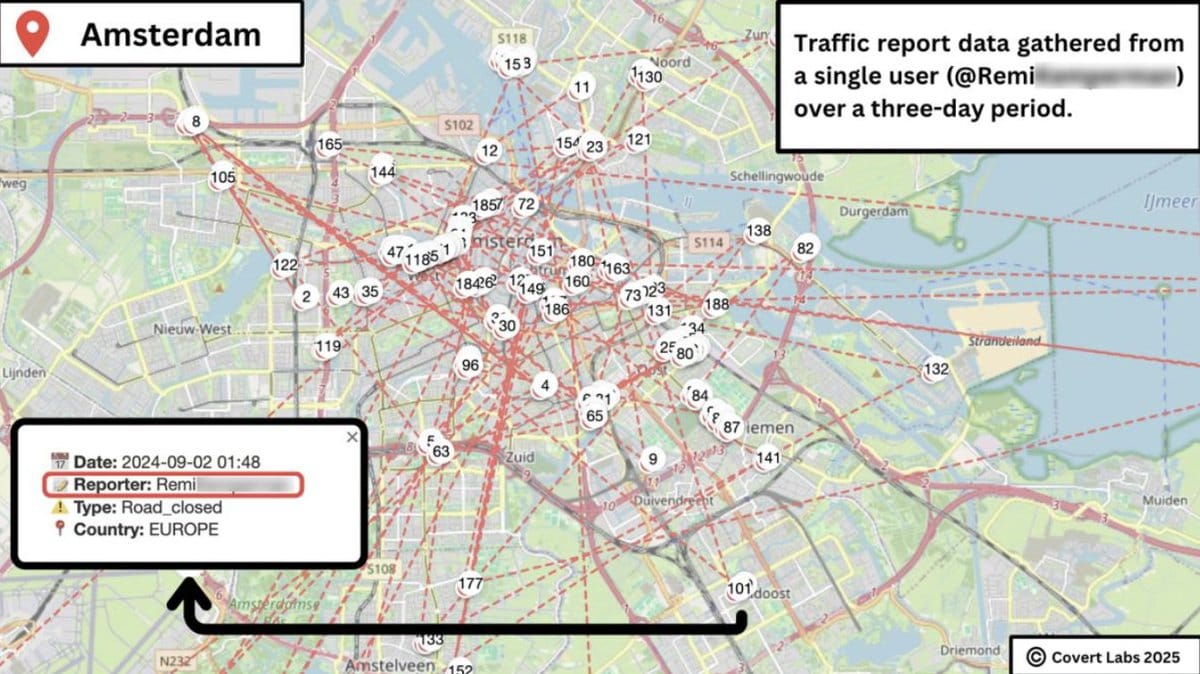
Waze Privacy Exposure: OSINT nerd Harry (@Harrris0n) revealed that Waze’s public map data could be scraped to track users' real-time locations and build detailed profiles, including home and work addresses. By cross-referencing usernames, these profiles could be linked to real identities. Although Waze patched the issue by removing usernames from public reports, the incident highlighted broader privacy concerns regarding the app's indefinite data retention and sharing policies with Google and law enforcement.
Key Takeaways:
Vulnerability Demonstration: Public map data (GPS coordinates, timestamps) was scraped to map out users' life patterns like home (overnight clusters) and work (daytime clusters).
De-Anonymization: Custom usernames were pivoted across platforms using OSINT tools to link anonymous reports to real identities and social media profiles.
Deanonymizing "Allocated" Users: Even random identifiers (e.g.,
world_xl868g9m) are vulnerable; unique home work patterns can be cross-referenced with public records to pinpoint specific individuals.Data Retention: Account deletion requests can take up to 2 months, leaving sensitive location history accessible during that period.
full analysis - https://x.com/Harrris0n/status/2014197314571952167
Vulnerabilities & Exploits & Hacks
Claude AI Scans PHP Supply Chain: The AI model identified 353 previously unknown zero-day vulnerabilities in the Packagist repository, marking a shift towards automated, high-volume vulnerability scanning. Find out more
SSH Side-Channel Leakage: Research reveals that distinct packet patterns in interactive SSH sessions allow passive observers to infer keystrokes and command lengths despite encryption. Find out more
Threat Hunting & Malware
Google Kills NTLMv1 with 8.6TB Rainbow Table: Google Cloud deliberately released a massive crack for Net-NTLMv1 to force organizations to abandon the broken protocol in favor of Kerberos or NTLMv2. Find out more | View Bucket
Other notable news
CrowdStrike Acquires Identity Startup Sgnl: The endpoint giant is buying Sgnl for ~$740 million to integrate "Zero Standing Privilege" and real-time authorization into the Falcon platform. Find out more
Palantir & Ukraine Launch AI Dataroom: A partnership with Ukraine’s Brave1 has created a secure platform using real-world war data to train AI models for battlefield applications. Find out more
📰Reports
Espionage & Counterintelligence
France’s "Spy School": The BBC takes a look inside the French university program specifically designed to train the next generation of intelligence officers. Find out more
Poland bans private Chinese EVs on bases: The Ministry of Defense prohibits private Chinese electric vehicles on military bases, fearing onboard sensors (LiDAR, cameras) could act as mobile surveillance for adversaries. Find out more
Denmark Intelligence Warns Against "WhisperPair": Danish Military Intelligence (FE) issues an urgent warning to stop using the "WhisperPair" app due to data harvesting risks linked to foreign state actors. Find out more
Milei Restructures Argentina’s Intelligence: President Javier Milei has signed a decree amending the National Intelligence Law, launching a sweeping reorganization of the country's intelligence apparatus. Find out more
Saab Launches Second Polish SIGINT Ship: Saab has officially launched the second Signals Intelligence (SIGINT) ship for the Polish Navy, significantly boosting Poland's electronic warfare and surveillance capabilities. Find out more
SOCMINT
Tiktok Saga vol…10000
TikTok Forms US Joint Venture to Avert Ban: To avoid a total shutdown, TikTok has finalized a US-majority joint venture led by Adam Presser as CEO, with Oracle officially overseeing all data operations. Find out more
TikTok Overtakes Traditional Social News: A new Pew Research Center survey reveals that 43% of U.S. adults aged 18–29 now regularly get their news from TikTok, surpassing YouTube (41%), Facebook, and Instagram.
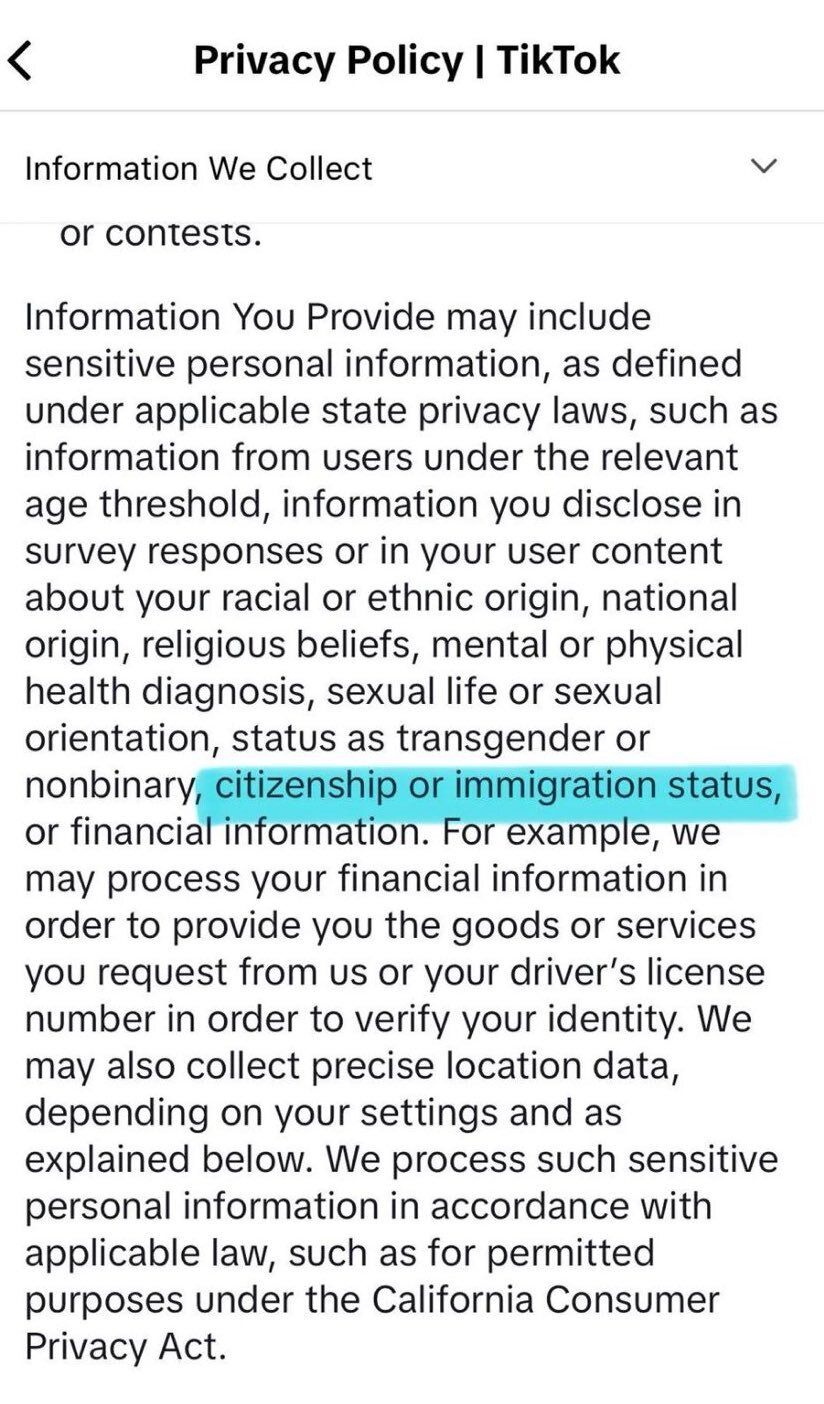
TikTok's New Policy Tracks Citizenship & Health: The platform's latest Terms of Service update explicitly allows the collection of highly sensitive data, including immigration status, religious beliefs, mental health diagnoses, and sexual orientation.
Discord Enforces Mandatory Age Verification: In response to tightening online safety laws, Discord is rolling out mandatory age verification protocols for users across parts of Europe and Australia.
"W Social" Rises as European Twitter Alternative: Unveiled at Davos by CEO Anna Zeiter - who sparked buzz by wearing a "Make Europe Great Again" hat - the Sweden-based platform positions itself as a "verified humans" alternative to X.
The "MEGA" Connection: Our latest investigation decodes the movement behind the slogan seen above. Led by Romania’s George Simion (AUR), these "European Trumpists" are directly transferring US MAGA tactics and slogans to influence key developments across the continent.
AI
AI Solves "Red Pixel" Disappearance: An AI system located a missing mountaineer in the Italian Alps by detecting a single red pixel—the climber's helmet—in drone imagery that human searchers missed. Read the full story.
Wikipedia’s Survival Strategy in the Age of AI: Wikipedia CTO Selena Deckelmann discusses how the platform is adapting its strategy to survive and maintain trust in an era dominated by generative AI.
The Bad: Qwen3-TTS (The "No-Limits" Cloner) Alibaba’s Qwen team has released Qwen3-TTS, an open-source voice cloning model. Unlike ElevenLabs or OpenAI, this model has zero safety rails.
The Threat: It runs fully offline. No verification, no "reading phrases," no cloud logs, no bans.
The Reality: A few seconds of audio ripped from YouTube is enough to clone a voice. For social engineering, the "CEO fraud" barrier to entry just dropped to zero.
OSINT Guest Section
In this edition, we sit down with the founder of OSINTIFYcon to discuss the philosophy behind the project and the specific tradecraft that powers their daily investigations.
From Tool Fatigue to Strategic Thinking
OSINTIFYcon was born… from a recurring frustration observed during years of hands-on fieldwork and training: practitioners were learning tools in isolation, chasing techniques that became obsolete within months. In a discipline where the pace of change is vertiginous, what was missing wasn't another list of links, but a space for strategic reflection.
I felt the need to create a place where OSINT practitioners could not only learn, but think together," the founder explains. "OSINTIFYcon is designed as a forward-looking observatory a telescope pointed at the future to help professionals anticipate shifts rather than constantly reacting to them.
The "Pillars & Workflow" Philosophy
This philosophy - prioritizing strategy over gadgets - directly informs their personal investigative toolkit. While powerful platforms remain central, the focus is on reducing cognitive friction and ensuring data quality.
The Core Stack: The daily workflow is built around Maltego, Social Links, and Effect Group. "Effect Group stands out as a simple, effective personal search engine with a crystal-clear interface that lets you move fast," they note.
The Data Add-ons: OSINT Industries and District4Labs (for breach data) serve as essential resources, used both standalone and integrated within Maltego transforms.
The Pillars: The workflow rests on a few stable foundations: SOCMINT, DNS Intelligence, and Corporate Mapping, supplemented by Telegram and Dark Web investigations to map contemporary threat ecosystems.
The AI Force Multiplier
Finally, the role of AI has shifted from hype to utility. It is no longer viewed as a shortcut, but as a "force multiplier" an accelerator for analysis, correlation, and hypothesis testing.
The Bottom Line: A powerful tool fed with weak data will always produce weak intelligence. When high-quality data and solid pillars are combined into a coherent logic, tools stop being gadgets and start becoming real instruments of intelligence.
📅 Event Details: OSINTIFYcon 2026
What: Virtual Conference & Specialized Training Sessions.
When: February 5, 2026.
The Agenda.
Tickets: Conference Tickets | Training Tickets
Special Offer: Use code AlicjaPROMO for the conference or AlicjaPROMOTRAINING for training sessions to get 30% off.
Note: More info about the event you will find in the previous issue.
Google Updates
Gemini Price Drop & Student Tier: Google lowers Gemini Advanced prices and introduces a free tier for verified students to democratize access to AI for academic research. Find out more
Apple Integrates Gemini into Siri ($1B Deal): In a massive annual deal, Apple will use Google's Gemini for complex reasoning in Siri, while local models handle privacy-sensitive tasks. Find out more
Google Meet Predicts Tardiness: A new feature analyzes your meeting history to predict arrival times, blending helpful utility with a hint of dystopian tracking. Find out more
Google Backs Sakana AI in Japan: Google invests in Tokyo-based startup Sakana AI to strengthen Gemini’s presence and capabilities within the Japanese market. Find out more
Darkweb
Google Kills Dark Web Report Bad news for casual monitoring: Google is shutting down its consumer "Dark Web Report" feature in February 2026.
Upcoming CyberSec / OSINT Events
Free
Webinars
OSINT Course for Journalists: January 27, 2026, 12:00 PM – 4:00 PM ET. Sessions are available in both English and Spanish. Find out more
Cyber Security Winter School (Zero to Hacking): Starting February 10, 2026 (Every Tuesday), 17:00 – 19:30 CET. Save the spot.
From Online Deception to Criminal Conviction: An OSINT-Driven Romance-Fraud Investigation: February 17, 2026, 12:00 PM EST. Sign up here.
Please note that participants must have a valid email address from a Canadian law enforcement or regulatory agency to receive an invitation to the session.
OSINT Investigation: Tracking Fentanyl Precursors in China: February 19, 2026, 16:00 CET. Find out more
Meetup
Cross-Community Meetup OSINT-FR, CyberV and Les Jeunes IHEDN | Paris (Afterwork): February 13, 2026, 19:00 CET at We Are Brewers.

CTF
Maltego Community OSINT CTF: February 7, 2026, 15:00 – 19:00 CET.