Hi Everyone,
First off, welcome to the 30 new subscribers joining us this week thanks to a recommendation from a French source 🇫🇷! It’s great to have you with us.
We are entering the season of ambitious New Year's resolutions. While the intent is good, we all know the pattern: over-planning, 'straw fire' enthusiasm, and eventual burnout by March. January is usually defined by oversized goals that quietly disappear when reality hits.
That is why, for the past few Januaries, I’ve flipped the script. Instead of adding more to my plate, I focus on a "Not-To-Do" list.
We are great at making to-do lists, but we rarely audit the friction points holding us back. To increase my focus, I’m ruthlessly cutting out the following:
Not sacrificing sleep to be a "night owl" (or for the early risers: not checking a phone to scrolling or emails the second you wake up).
Not saying yes to every opportunity (If it’s not a "hell yes," it’s a no).
Not setting goals without systems: I used to lose flow when my goals outpaced my energy. Now, inspired by Atomic Habits, I focus on the "how" rather than just the "what" to maintain consistency.
Identify your time-wasters and energy drainers.
Your "Not-To-Do" list is just as crucial as your "To-Do" list.
Less noise. Better judgment. Cleaner workflows.
Now, Let’s dive into this week's news.
Cybersecurity News
Red Team Campaign Planner (RTCP) is live: A new tool designed to simplify the time-consuming process of creating adversary emulation plans. It streamlines actor identification and TTP mapping, replacing manual spreadsheets with a guided workflow. Find out more | Watch Demo
Deception in Cyber Counterintelligence: Resecurity deployed digital "honeytraps" to identify members of "ShinyHunters"→now rebranded as "Scattered Lapsus$ Hunters" (SLSH) linking them to "The Com” short for 'The Community') a predominantly English-speaking ecosystem of young, ego-driven cybercriminals. Find out more
Vulnerabilities & Exploits & Hacks
Instagram “17M leak” debunked - old data, not a new breach
The rumored “17M Instagram user leak” is not a new hack (as firstly reported Malwerbytes) but a recycled combo list compiled from infostealer data and publicly scraped API information from 2022–2024. Analysis shows the original dataset was created in 2022 and circulated in 2023.If this were a genuine new breach, it would likely appear in Have I Been Pwned, which it does not. The issue has also been analyzed publicly by Troy Hunt. Read analysis and Thread1 & Thread2.
Separately, Instagram fixed a bug that allowed attackers to trigger mass password reset emails. If you didn’t request a reset, you can safely ignore these messages.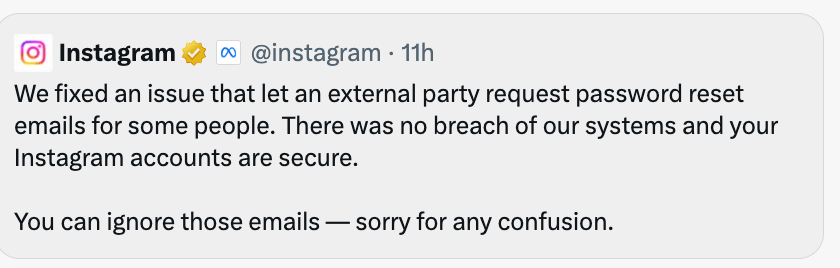
What you should do (practical steps)
Ignore unsolicited password reset emails - do not click links inside them. According to Instagram’s Help Center, legitimate messages are only sent from addresses ending in @mail[.]instagra[.]com.
Change your password manually via Instagram settings if you want a precautionary reset.
Enable two-factor authentication (2FA) to reduce account takeover risk.
Check your email on Have I Been Pwned to see if it appears in known breaches (unrelated to this case).
Threat Hunting & Malware
Jihadist Manual Uncovered by Infostealers: An analysis of compromised logs from a machine in the West Bank revealed "The Art of Recruitment" a structured manual for radicalization. This discovery highlights how infostealers expose not just credentials, but deep operational intent and ideology. Find out more
Fusing CTI with Threat Hunting: A new guide from Feedly and Team Cymru argues against operating in silos. It details a workflow where CTI provides context to hunters, and hunters provide feedback to CTI, shifting the focus from "chasing alerts" to "anticipating threats." Find out more
📰Reports
The Future of OSINT — Maltego breaks down emerging trends, the integration of AI in investigations, and the shifting regulatory environment. Read more
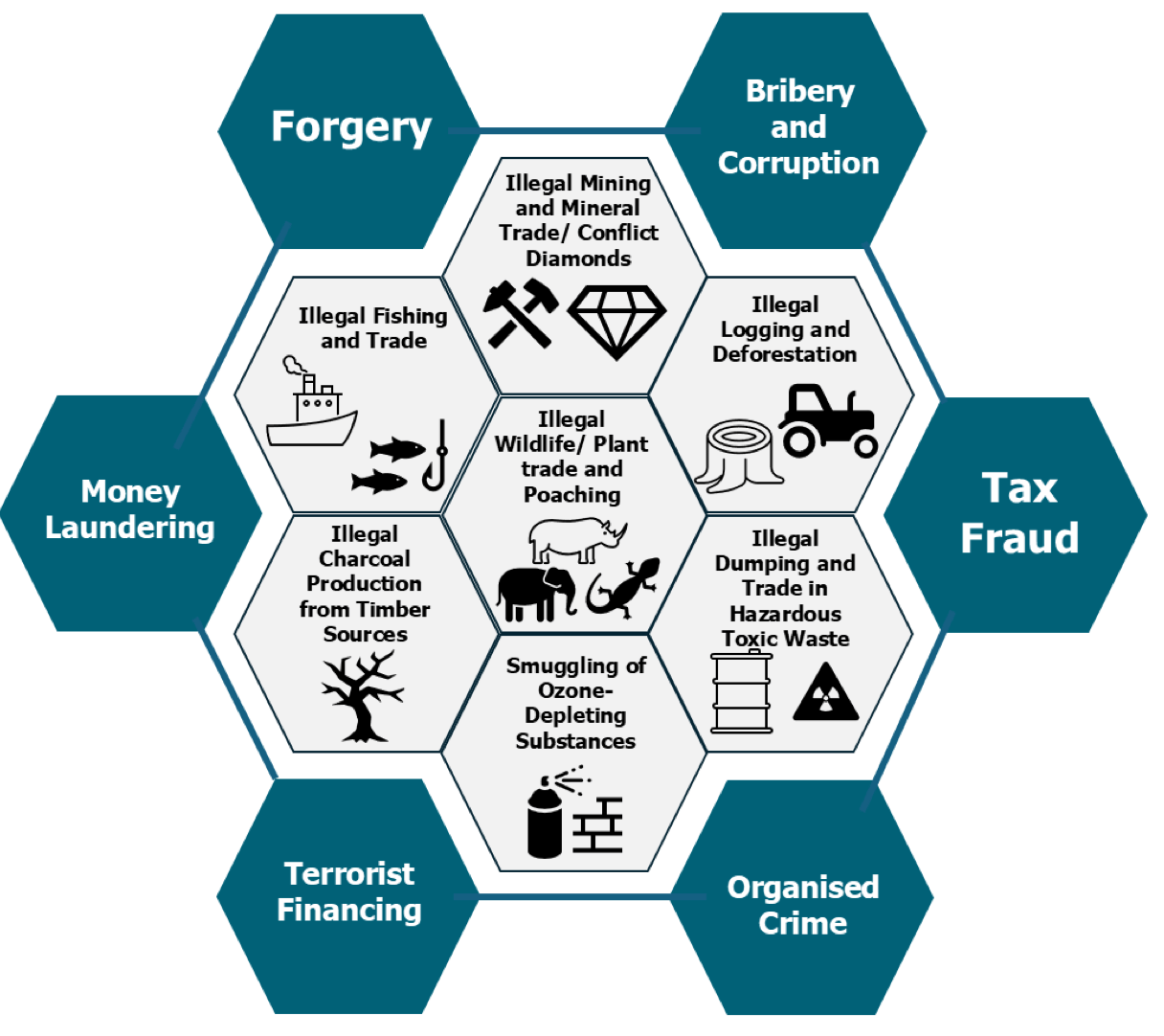
Environmental Crime Typology — The Isle of Man Financial Intelligence Unit (FIU) releases new indicators and case studies to help identify financial flows linked to environmental crimes. You can read it here.
Espionage & Counterintelligence
Berlin Grid Sabotage: The anarchist group "Vulkangruppe"- previously known for attacking Tesla's Gigafactory - claimed responsibility for a massive power outage in Berlin, prompting an anti-terrorist investigation. Find out more
Civilian Espionage in Norway: The Norwegian military reports Russia is increasingly using civilian fishermen and tourists for espionage near the border a classic "gray zone" tactic that complicates traditional counter-intelligence efforts. Find out more
Russia–Sudan Strategic Pivot: Moscow’s "Africa Corps" is shifting support to the Sudanese Armed Forces (SAF) to accelerate a naval hub deal in Port Sudan, while maintaining a dual-track presence near resource sites. Find out more
Balticconnector Arrests: Finnish authorities arrested two foreign nationals (linked to the Chinese vessel NewNew Polar Bear) accused of deliberate sabotage regarding the 2023 pipeline damage. Find out more
Intellexa Sanctions Lifted: The US Treasury quietly removed sanctions on key individuals associated with Intellexa (vendor of "Predator" spyware). Find out more
Russian Sub Tracking: Declassified UK imagery reveals a Russian submarine tracking the research vessel Yantar while it monitored critical subsea pipelines between the UK and Ireland. Find out more
SOCMINT
AI
ChatGPT Health: OpenAI has launched a dedicated "Health" workspace for Plus/Pro users. It is designed for wellness conversations with strict privacy controls (data is not used for training). Find out more
Grok & Safety Concerns: The Internet Watch Foundation (IWF) reports that Elon Musk’s AI tool, Grok, has been used by bad actors to generate child sexual abuse imagery (CSAM). Find out more
Meta Acquires Manus: Meta has acquired Manus, a Singapore-based AI startup (originally founded in China), for ~$2 billion.
What is Manus? It is an "agentic" AI platform. Unlike a chatbot that just talks, Manus is an "agent" that does things it can autonomously execute complex workflows (e.g., "plan a travel itinerary and book the tickets" or "research this stock and create a report").
The Conflict: The deal has reportedly sparked a probe by Beijing, as the company has Chinese roots, highlighting the growing geopolitical tension over AI talent and technology transfer. Find out more
OSINT Section
Tools
Topaz Labs: An AI-powered suite for upscaling and enhancing low-resolution images and videos. Visit
Sanction Blockchains: A resource for tracking Bitcoin addresses linked to sanctioned entities, useful for financial investigations. Visit
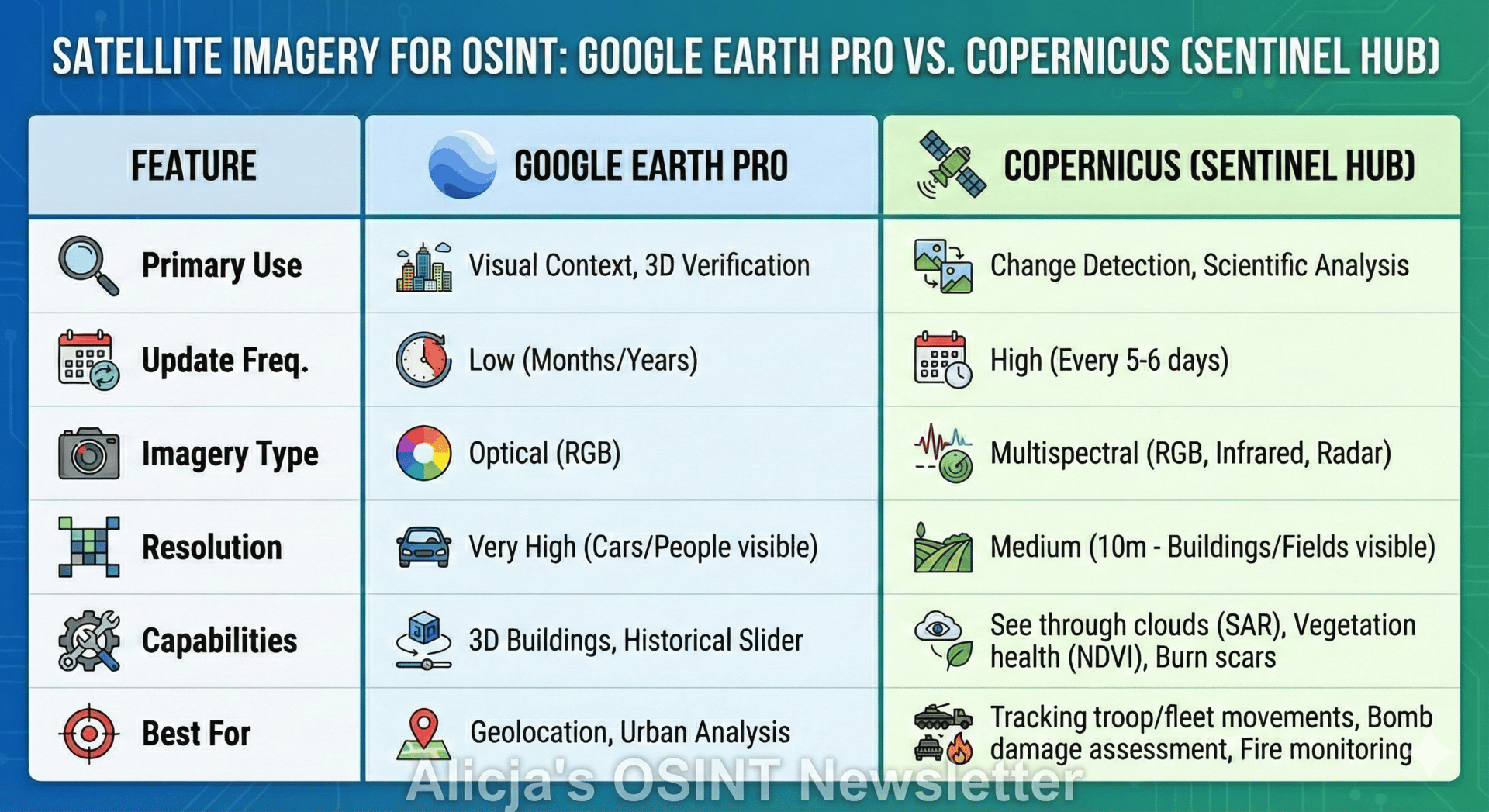
Feature: Copernicus vs. Google Earth Pro
Why you need both in your arsenal.
Many analysts default to Google Earth Pro, but for active conflict monitoring or environmental analysis, Copernicus (Sentinel Hub) is often superior.
Use Google Earth to see what a place looks like.
Use Copernicus to see when something changed or what is hidden (e.g., using Infrared to spot camouflage or Radar to see through storms).
For LEA only 🛡️
Deconflict launches "Signal": A new shared intelligence layer designed to help verified LEA and compliance teams deconflict cryptocurrency investigations.
The Problem: Agencies often investigate the same wallets/clusters in isolation, wasting resources.
The Solution: Signal allows agencies to query investigative-grade address intelligence and receive real-time notifications of overlaps without sharing PII or case narratives. Request Access | Read Announcement
Webinar: Building a Digital Profile (CDR & IPDR): A free webinar focusing on the tradecraft of using communications data (Call Detail Records, IP logs, PCAP) to identify the person behind the device not just the phone itself. Register
Google Updates
Gmail Enters the Gemini Era: Google has integrated Gemini into Gmail, enabling natural language inbox search ("Q&A") and smart summaries to accelerate email triage. Find out more
Wiz Deal & EU Sovereignty: Experts warn Google's acquisition of Wiz could undermine EU cloud sovereignty and complicate data compliance for European markets. Find out more
Upcoming CyberSec / OSINT Events
Free
Webinars
Exploring the Corporate Use of AI in India Date: January 22 (11:30 AM IST) A discussion on the regulatory and operational landscape of AI adoption in the Indian corporate sector. Register
Crypto Compliance & Investigations (ACAMS) Date: January 23 (12:00 PM EST) Webinar focused on AML standards and tracking illicit flows in the crypto space. Register
[for Portuguese speakers] Enhancing Suricata with MISP: Practical Threat Intelligence Integration: January 28 (5:00 PM CET) A hands-on webinar where Cleber Soares demonstrates how to enhance detection and threat intelligence capabilities by integrating Suricata with the MISP framework. Register
CTF & Challenges
Trace Labs: Call for Coaches & 2026 Roadmap Trace Labs has announced its plans for 2026, which include four full-scale Search Party CTFs (February, May, August, October). They are currently recruiting coaches for the upcoming February event to handle the expected high turnout. Read more | Apply to Coach
Info from the Tracel abs team: Unlike our last CTF, this one will be full-scale, so we’ll need plenty of coaches. We had a pretty high no-show rate last time, so nobody was bored! If you haven’t judged or coached for a while, we’ll make sure you get the link to the orientation video as well as the coach briefing. We will be onboarding some new coaches this time around, so there will be new folks in the mix! I hope to see many of you in February!
ImaginaryCTF: Daily Challenges Status: Ongoing Fresh cybersecurity and CTF challenges released daily across various categories to keep your skills sharp. Play | Archives & Writeups
UK OSINT Community: OPERATION ECHO Status: Live Now A new five-part, spy-themed OSINT weekly challenge. It starts with a seized hard drive and a single image of a London hotel. No hints, no shortcuts you must solve each stage to unlock the next. Start Challenge | Join Discord
Freemium
SANS Cyber Threat Intelligence Summit 2026 Date: January 26–27 (Virtual) The annual "Must-Attend" event for CTI professionals. Summit talks are typically free to watch virtually. Register
Trainings
[for French speakers]Cyber4SME: Security Awareness Workshop Format: Freemium Trainings -Brussels/Virtual - Workshops dedicated to improving cybersecurity posture for journalists. Register
Writeups
OSINT Industries Christmas CTF Write-up: A comprehensive community breakdown of every challenge, covering real-world techniques like GEOINT and entity resolution—essential reading for methodology. Read Write-up
Investigation Numérique (Playlist): A curated French YouTube series on digital investigation tradecraft (auto-captions available for non-French speakers). Watch
Advent Challenge Solutions (Days 1-8): Detailed walkthroughs and solutions for the first week of the recent OSINT challenges by David Varghese. Read
🙃Bonus
[Job ad] Meta Anti-Scraper: Meta is seeking a seasoned investigator to analyze and mitigate scraping abuse across all its products; AI experience is a plus. Apply